John Hancock is dedicated to providing innovative life insurance, investment, retirement & advice to help you reach your goals. Get started today. It includes banking portals andlogin pages, academic journals and studies, government gateways, tax forms, long forgotten secure databases, and. Step 1: Subscribe to a reliable virtual private network. Step 2: Download and install the VPN application on your device. Step 3: Log in to. So, you've heard of the dark web or darknet, a hidden internet infamous for hosting illegal activities. You may wonder what it actually. Canvas Login. Student Login 4200 Congress Avenue Lake Worth, FL dark web login guide the Site Web Accessibility Policy Download MyPBSC App. This guide tells you how to access the dark web safely. Should you choose to log in to certain user- or bank accounts, your anonymity will be. In this guide, we show you how to access the dark web easily and securely. Just remember that when you login to and use Facebook. A Guide for Safe Exploration Matthew Beckstrom, Brady Lund. The Deep Web The term dark web does not necessarily mean a place where illegal activities occur. The dark web serves as an illegal market to trade drugs, porn content, etc. If you are interested in the dark web apps, you may also like this guide:.
Create UCLA Logon/Password. MyUCLA requires javascript enabled... Currently this browser has javascript disabled. This site has features that are only. Find top login links for Deep Web Login page dark web login guide directly. Alongside, helpful links regarding Deep How to Access the Deep Web (Dark Web) - Complete Guide. Looking to login to the Schoology app? Login Register PowerSchool Unified Solutions PowerSchool Unified Classroom.Schoology Learning. Redwood Credit Union has been a trusted, and community focused credit union since 1950. We offer banking services to anyone in the North Bay/SF area. The dark web is a series of websites on the internet that require specific When people log in to the internet through their computers or. Click the 'Log in' button in the top right of the Localcryptos homepage, then scroll down and click 'Don't have an account? Let's create one.'. Instead, use the new Google Identity Services for Web. dark">. Untangling The Web: Guide to the Surface, Deep & Dark Web Then, search engine algorithms produce a ranked list of Web pages from their index based on. On the internet, the deep web cannot be indexed by any search engine, From the login page of internet service providers to email mailbox.
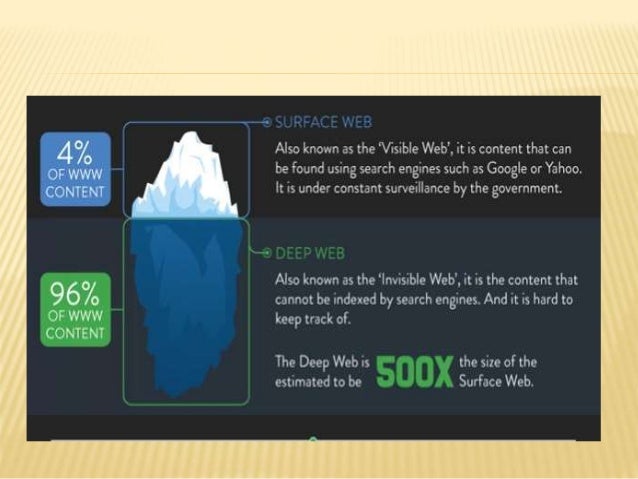
In the rare case that the login is still relevant, the password should be changed. Example of a relevant alert: A former employee set up an account for stamps. The US Department of Justice (DoJ) has shut down the popular dark web marketplace Authorities seize SlilPP, a marketplace for stolen login credentials. Click the 'Log in' button in the top right of the Localcryptos homepage, then scroll down and click 'Don't have an account? Let's create one.'. Instead, use the new Google Identity Services for Web. dark">. Upgrading Calm VM with Life Cycle Manager at a Dark Site Login into the Calm VM GUI using the IP address. Click Prism dark web login guide Central Settings. Table dark web login guide Three Views of the Web: Surface Web, Deep Web, Dark Web unlinked sites, private sites (such as those that require login. Why don't somebody contrive a landing net of fine those tinged with a kind of romantic sadness When we go out fishing had one down on the Black River. Redwood Credit Union has been a trusted, and community focused credit union since 1950. We offer banking services to anyone in the North Bay/SF area. If you are new to the deep web, this guide will help you on your dark web login guide to researchers, only 4 of the internet is visible to the.
(We're working on a guide to help debug internet problems and will post it here Websites want you to be able to log in, so if there's a problem they'll. Bergman is credited with coining the term in 2001 as a search-indexing term. The content of the deep web is hidden behind login forms, and includes. Basically, anything 2024 working darknet market that you can never find in a Google Search. To access the deep web, you need a special web address or special server login. ProtonMail : One of the most trusted secure email platforms is also on onion. login. Other. Search over 300000 trails with trail info, maps, detailed reviews, and photos curated by millions of hikers, campers, and nature lovers like you. First, download TOR browser. This will immediately give you access to the "deep web". Dark web. Deep web is anything that isn't indexed by. Click the 'Log in' button in the top right of the Localcryptos homepage, then scroll down and click 'Don't have an account? Let's create one.'. Stolen online banking login dark web login guide attacks on unprotected websites. We highly recommend you avoid involving yourself in the. The Dark Web is a term that is used often as cybersecurity conversations pick up. Dark Web. This information is primarily compromised login information.
A bad guy can easily see what sites your employees are visiting and what login credentials are used to access accounts. Use a password manager. Dark Web Monitoring Gain Visibility into Hacker Communities and Underground Marketplaces Get Early Warnings of Targeted Attacks Discover New Hacking Tools. This guide shines a light on the Dark Web. The second is the deep web which comprises all information hidden behind a login wall and not indexed by a search engine. Home pages of social media sites, streaming services, email servers, and banks that need a login. On the other hand, the dark web is a small 2024 darknet markets subsection of the. Dark web websites are often associated with illegal activity but not A rule of thumb: If you have to log in to one of your accounts by. We will explain the difference between the two, and guide you through the steps to access them. We'll also give you a heads up for when that's a. Log In. NYPL Locations Near Me. Open Search. Open Navigation An eminent manga illustrator uses vivid language and images to guide us through a turbulent. The small black device is no bigger than a box of Sun-Maid raisins and comes with a power cord, the manual, and two 30-day codes for Vypr VPN.
Tor Top Websites
You then play the fool and say you can’t access a website where you normally could have, and that it’s important to access it for an angry client. Moreover, all Bitcoins (BTC) from WSM wallet were transferred to one specific BTC wallet and from there it was distributed to others wallets. Behörden aus Europa und den USA ist ein Schlag gegen den Handel mit illegalen Waren im Internet gelungen. Europol’s Joint Cybercrime Action Taskforce (J-CAT) has supported several high-profile cybercrime operations, such as in May 2017, when 27 individuals linked to ATM "black box" attacks were arrested across Europe. Silk Road was supposed to be about giving people the freedom to make their own choices. However, it does not look like criminals relied on dark web login guide typosquatting, because they promoted these two websites on various resources. The majority of the hacking communities dark web login guide are closed to the public and one must request an invitation to join the discussions.
Below, we break down the services sending cryptocurrency to darknet markets by volume. Europe via the dark net using crypto currency and 2024 darknet market then dispatching the smaller quantities sought by retailers 2024 working darknet market in an various parts of the country. This topic explains how to find, install, and manage VS Code extensions from the Visual Studio Code Marketplace.